Application vulnerabilities are a major concern in the world of cyber security. Malicious attackers can exploit these flaws, weaknesses, or gaps in the code —whether in the configuration or design of a piece of software— to compromise the application’s security. This is why it is so important to detect code vulnerabilities and apply patches.
We use StackSpot AI to boost application security. Keep reading to understand the tool and learn how we do it.
What are application vulnerabilities?
Application vulnerabilities can vary in nature and impact. They can allow hackers to carry out a wide range of malicious activities, such as unauthorized access to data, information manipulation, service interruptions, or execution of arbitrary code on the compromised system.
These vulnerabilities can come from:
- Coding errors: Programming flaws, such as SQL injection and cross-site Scripting (XSS), among others.
- Lack of Access Control: Inadequate permissions that allow unauthorized access to data or functionalities.
- Insecure Settings: Incorrect or insecure settings that attackers can exploit.
- Vulnerable Dependencies: Libraries or components that are outdated and susceptible to threats.
Regarding frameworks for analyzing and correcting vulnerabilities, the main reference is OWASP, a global community focused on improving software security. The OWASP Top 10 lists web application security vulnerabilities, updated regularly to include the most pressing threats.
OWASP
Multiple factors are behind the importance of and respect for OWASP:
- Authority and Experience: OWASP is recognized worldwide for its expertise in web application security. The organization brings together security professionals from all over the world to contribute to its research and guidelines.
- Awareness: The list serves as a starting point for developers, security engineers, and IT decision-makers to become aware of the most critical vulnerabilities that can affect web applications, empowering them to prioritize mitigation efforts.
- Education and Guidance: Besides identifying vulnerabilities, the OWASP Top 10 provides detailed recommendations on preventing or mitigating these risks, helping organizations develop more secure software right from the start.
- Security Standard: Many organizations and compliance frameworks adopt the OWASP Top 10 as a minimum standard for web application security practices. Following the list can help organizations meet regulatory and compliance requirements.
- Continuous Improvement: The list is updated regularly to reflect changes in the threat landscape, ensuring that organizations are aware of emerging vulnerabilities and the best practices against them.
Ultimately, following OWASP significantly reduces the risk of security incidents, such as data leaks, security breaches, and cyberattacks.
This initiative protects confidential information and users’ privacy, safeguards the organization’s reputation, avoids legal and financial penalties associated with data breaches, and improves trust among the software’s customers and users.
Knowledge of the OWASP Top 10 will be essential for effective detection of code vulnerabilities and fixes using StackSpot AI.
Application vulnerability analysis tools
Several tools on the market are capable of analyzing and detecting application vulnerabilities, and even showing the steps needed to correct them. However, in addition to the high price, developers struggle to understand the vulnerability and fix the code by implementing the necessary changes.
With great versatility, StackSpot AI allows quick and effective vulnerability fixes with the help of artificial intelligence. Find out how.
About StackSpot AI
StackSpot AI is a code assistant capable of using your context, knowledge bases, and technological decisions to generate more assertive, high-quality suggestions. You can:
- Optimize the Developer Experience (DevEx) and increase your team’s productivity.
- Receive more assertive code suggestions.
- Create quick commands to automate repetitive tasks.
The tool makes it possible to create code efficiently and securely based on your project or company’s programming language, frameworks, and stacks. You can feed customized knowledge bases, document, explain, refactor code, and create test cases through it.
Fixing application vulnerabilities with StackSpot AI
This article describes how we used StackSpot AI to detect and fix common code vulnerabilities.
To do this, we followed the steps below:
- Create a “Quick Command” using StackSpot AI. This tool’s features allow you to centralize and orchestrate a series of command prompts, use a knowledge base, and call external APIs.
- You can feed a Knowledge Source with information and code vulnerability fix snippets. This step is optional because the prompt will usually be enough. Use this option for specific cases or zero-day vulnerabilities.
- Provide a base of customized company parameters (e.g., AWS account, region, naming standards, etc.).
- Perform prompt engineering to obtain the best results for our purpose with the artificial intelligence software.
- Create a step to integrate with GitHub to automatically create a patch issue for the vulnerability found.
- Publish the Quick Command in a StackSpot Studio.
- Add this Studio to a StackSpot Workspace.
The Quick Command will search for vulnerabilities based on the OWASP Top 10, explain the vulnerability, show the code snippet where it applies, and suggest a code fix.
Code vulnerability fix demos
We used Quick Command to test the hypothesis and demonstrate that it was possible to identify and fix code automatically.
Let’s run a Quick Command on the codes below that contain known vulnerabilities. The screenshots show the corrected code suggested by it.
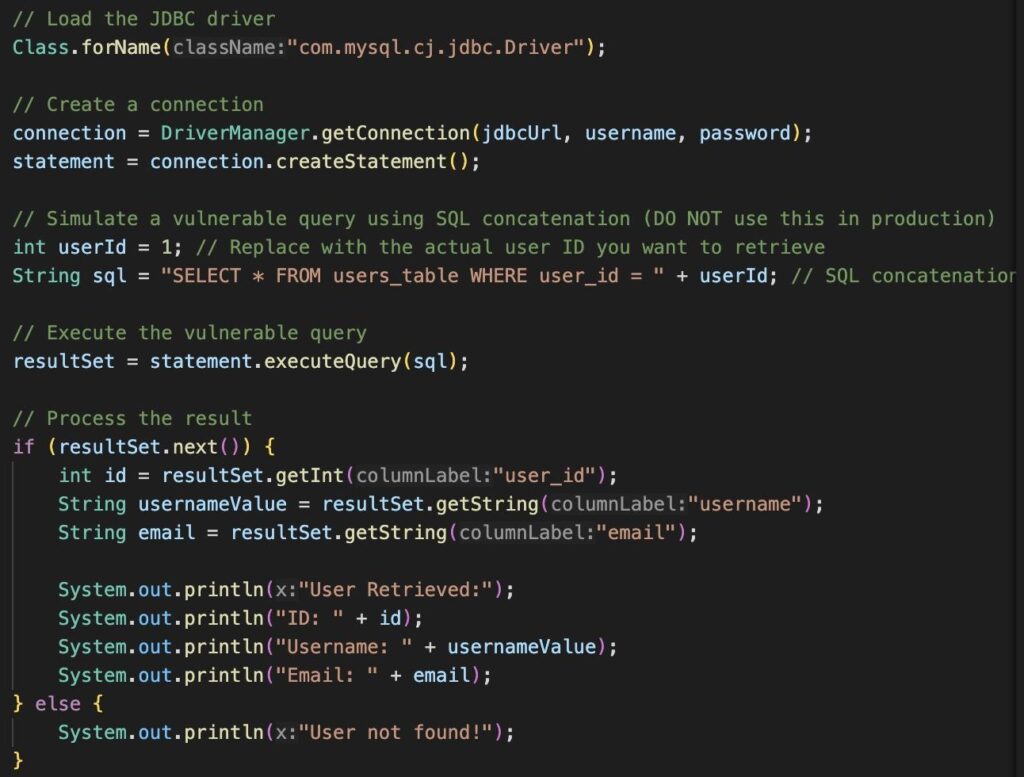
Example 1: SQL Injection vulnerability in the Java language
SQL Injection: SQL injection is a cyberattack technique often used to exploit system vulnerabilities that interact with databases through SQL queries.
This technique involves inserting malicious SQL code into data input fields, such as web forms, URL parameters, cookies, etc. When the web application does not properly sanitize or validate this input data, the database system can execute the inserted SQL code, allowing the attacker to access, modify, or delete data from the database or even execute commands on the server.
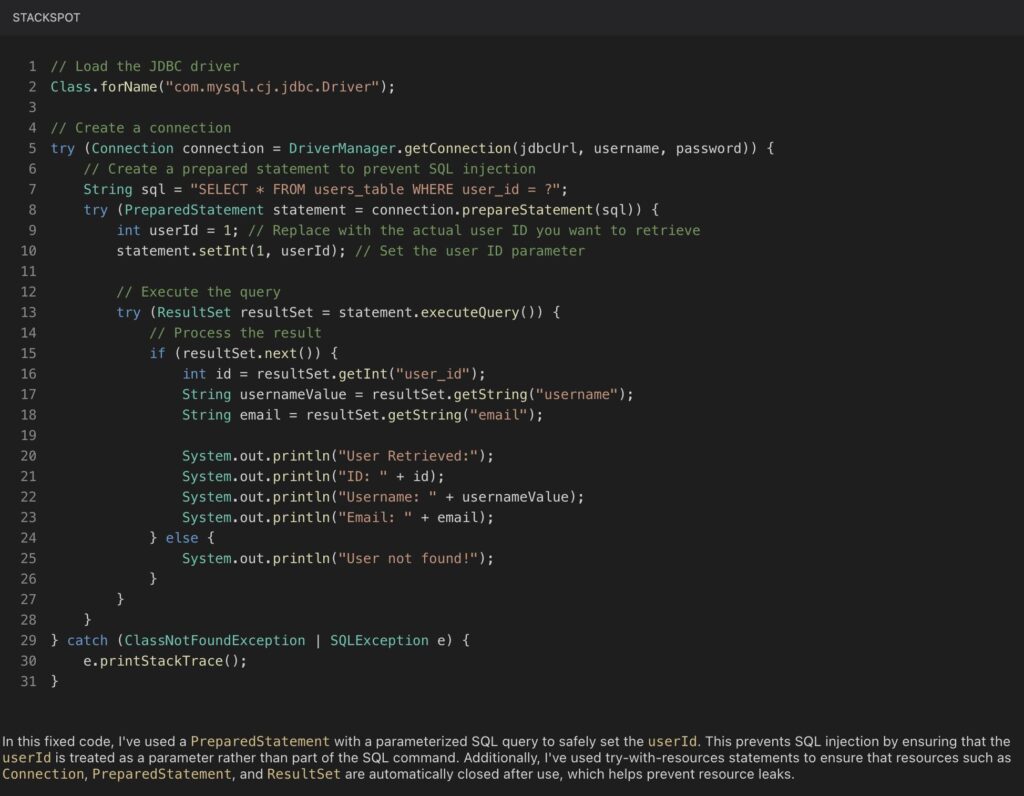
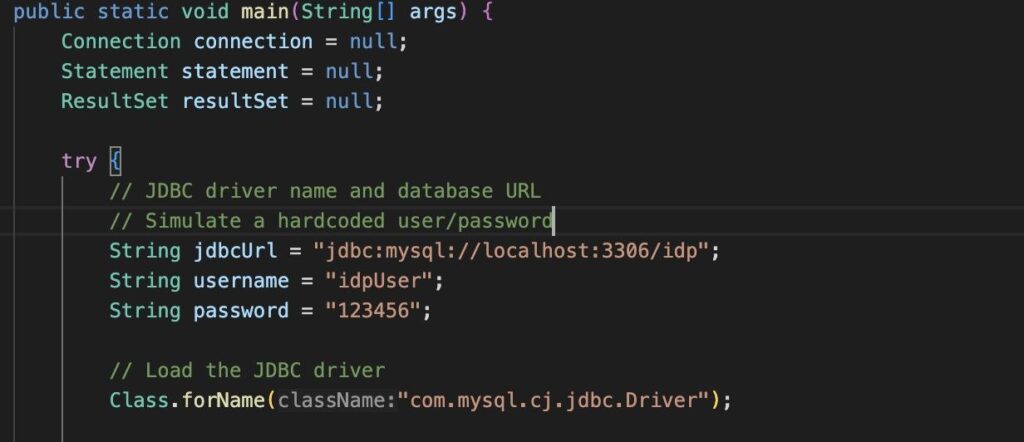
Example 2: Hard-coded credentials vulnerability in the Java language
Hard-coded credentials: Hard-coded credentials refer to the practice of including authentication information directly in the source code of a program or application instead of storing it securely in a protected location, such as a secure configuration file or secrets manager.
These credentials usually include usernames, passwords, access tokens, API keys, or other authentication information. When this information is embedded directly in the source code, it can be easily accessed and viewed by anyone who has access to the code — like a developer, code reviewer, or even a potential attacker who has gained access to the source code.
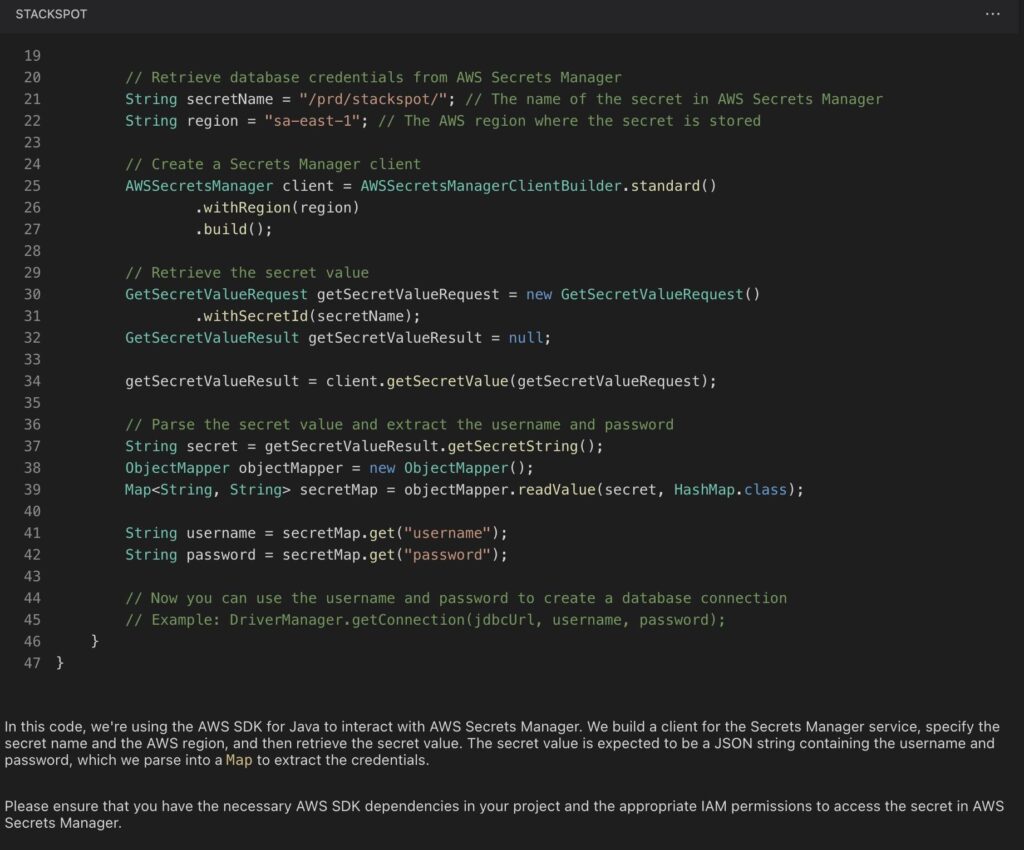
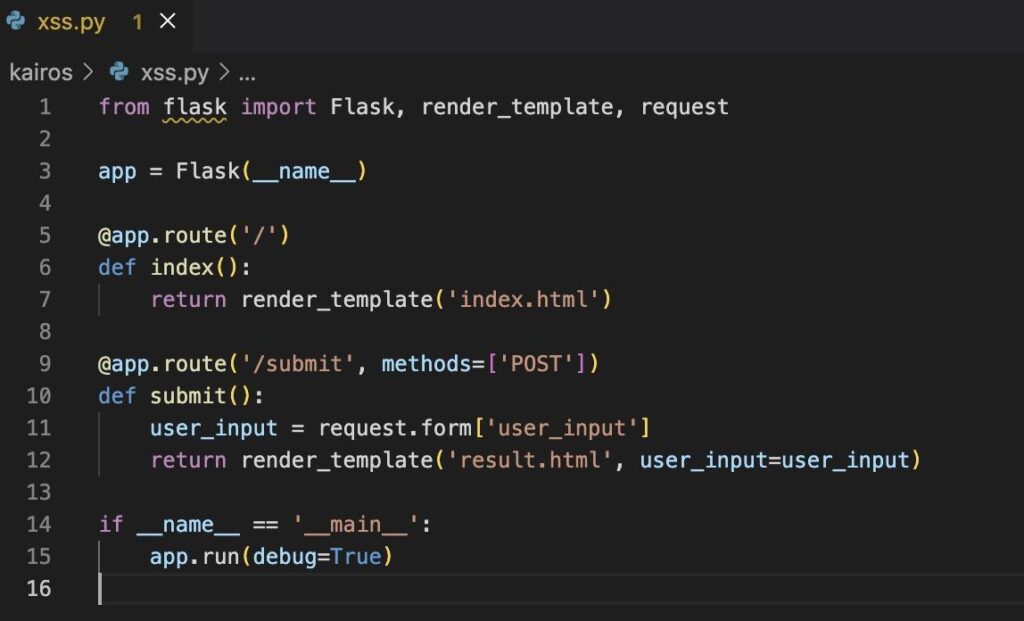
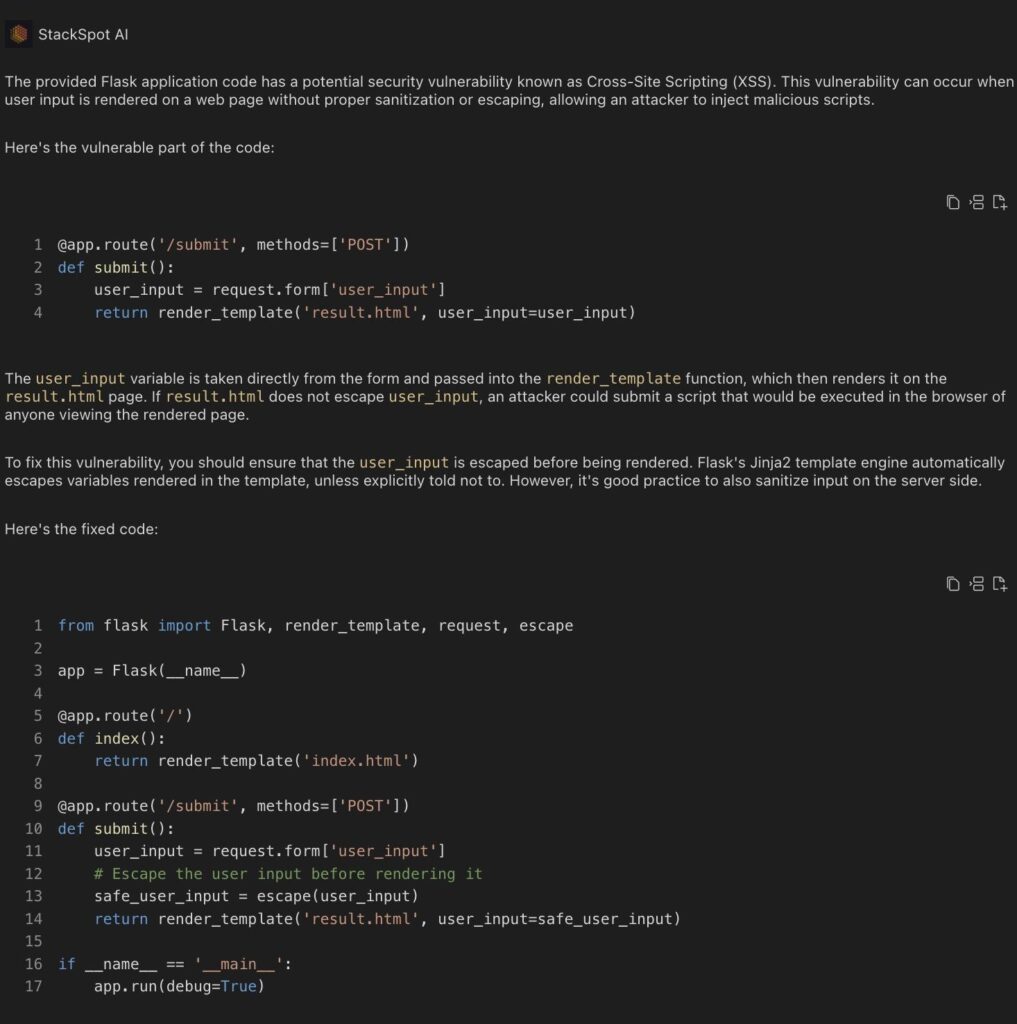
Example 3: Cross-Site Scripting (XSS) vulnerability in the Python language
Cross-site scripting (XSS) is a security vulnerability in web applications that allows an attacker to inject and execute malicious scripts in an end user’s browser. This situation can happen when untrusted data is inserted into a web page and then executed in the browser of other users, compromising their security and privacy.
XSS attacks can be used for session theft, redirecting to malicious sites, stealing cookies, and displaying unwanted content, among other damages.
Example 4: XML external Entity (XXE) vulnerability in the Python language
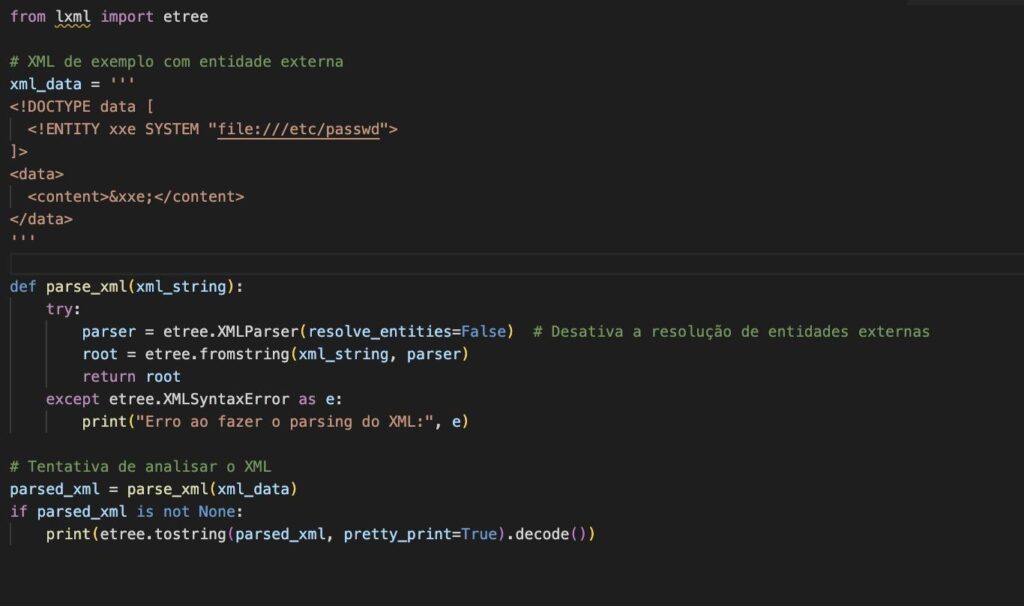
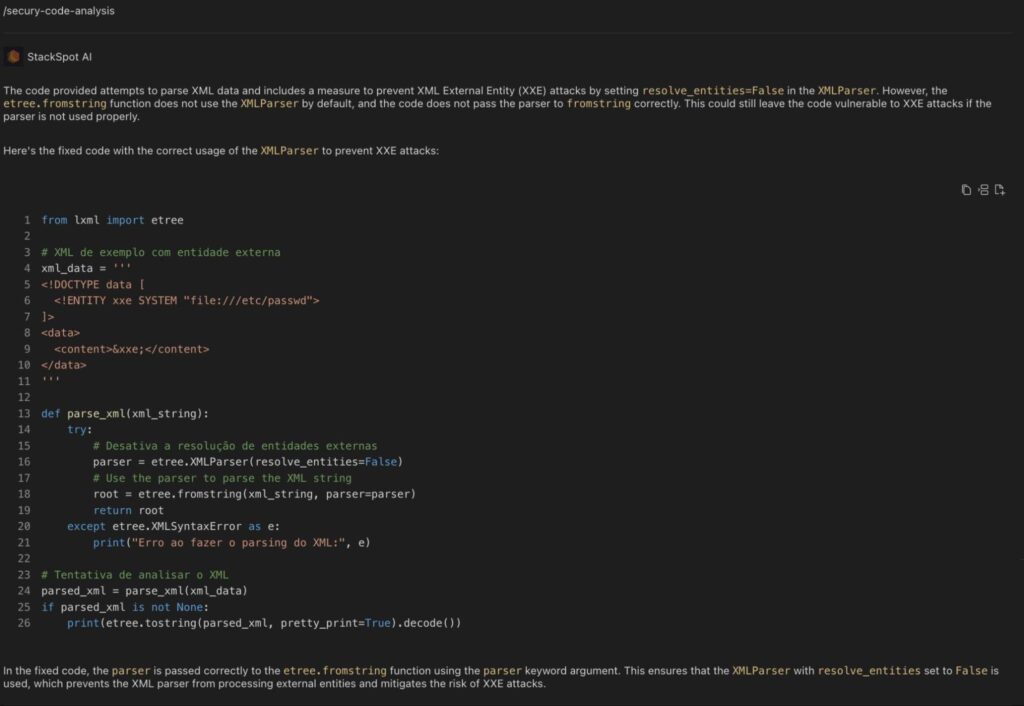
XML External Entity (XXE) is a security vulnerability in systems that process XML documents. This vulnerability occurs when an application processes XML entries that contain references to external entities, allowing an attacker to access system resources or perform unwanted actions.
In an XXE attack, an attacker can exploit this vulnerability to read system files, interact with internal services, execute remote code, and even cause denial of service. The consequences can be severe, including leakage of confidential data and system compromise.
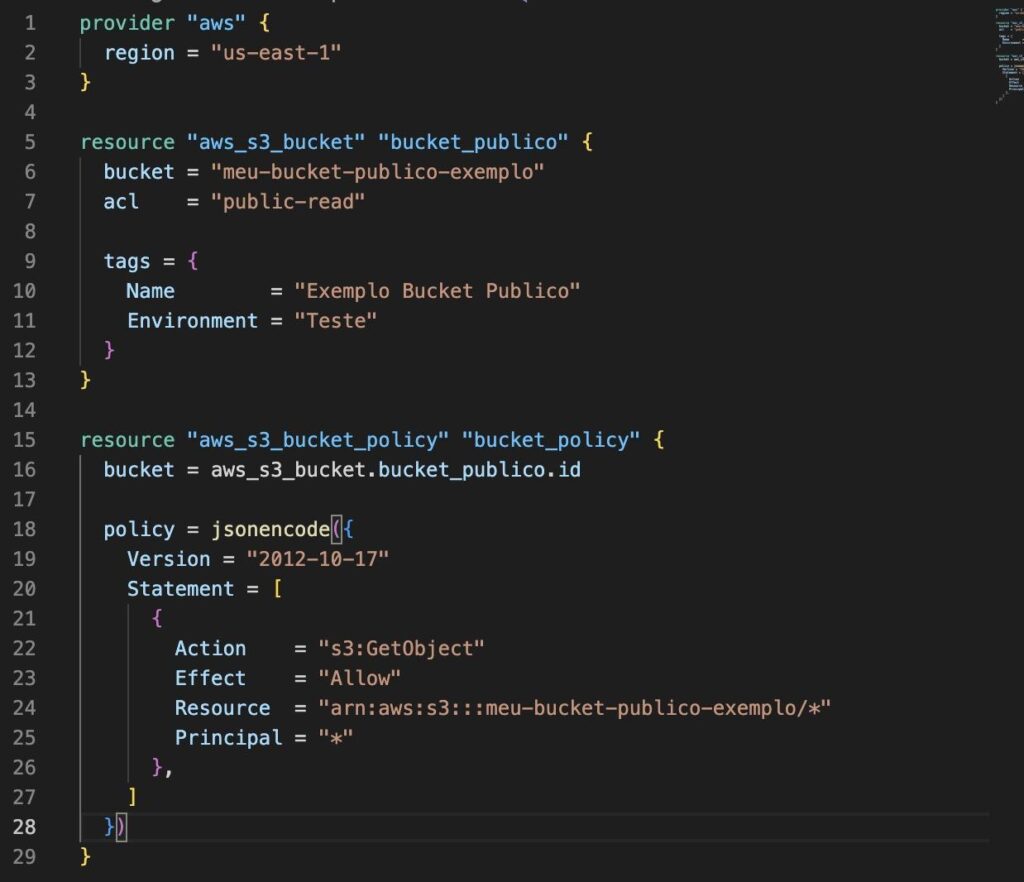
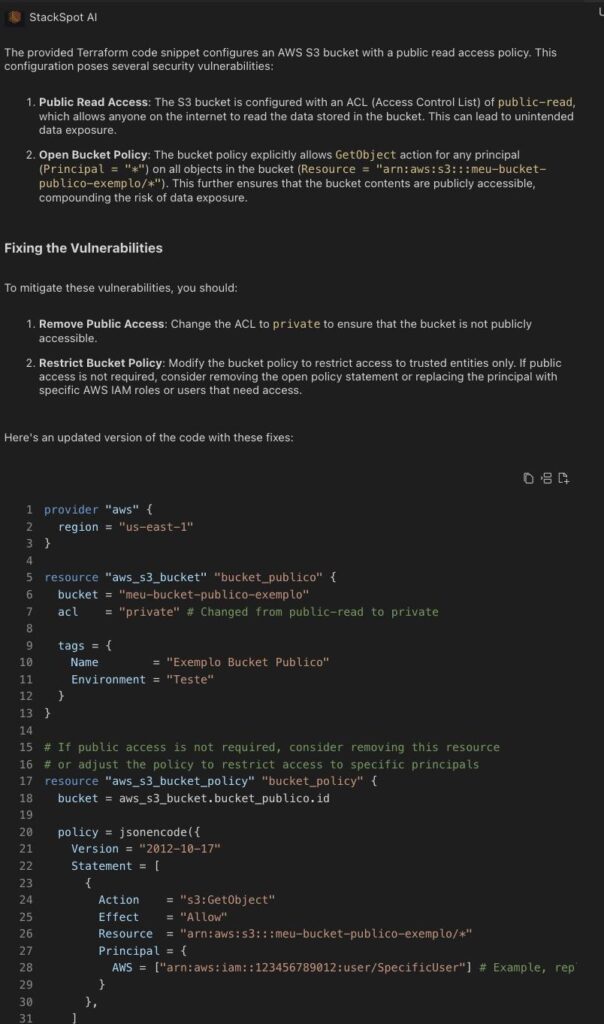
Example 5: Creating a public bucket with a risk of data leakage in the Terraform language.
Public bucket: While not exactly a vulnerability, it is not recommended, except in specific cases.
Check out all the examples of fixing application vulnerabilities with StackSpot AI in this video and subscribe to our YouTube channel:
Conclusion
StackSpot AI demonstrated remarkable efficiency in detecting vulnerabilities and creating patched code across various programming languages. Leveraging artificial intelligence with context, it offers the advantage of using customized parameters in a fix (language, frameworks, parameters, standards, policies, etc.).
This way, it can create the code that best suits your project and your organization.
As it is possible to feed the AI with knowledge bases, StackSpot AI is kept up to date even if the LLM database is limited to a period. Its efficiency surpasses that of conventional market tools thanks to its ability to suggest corrected code with context and provide explanations and insights related to security.
Did you enjoy the content about Application Security and want to know how StackSpot AI can be used in your scenario? Request a demo!






